Found at: https://forum.kodi.tv/showthread.php?tid=224196
Pasting here for safekeeping:
2015-04-12, 17:08 RavynDarkcraft
Hello Community,
So, a while back I ran into some infuriatingly annoying issues related to HDMI audio from my HTPC to my Onkyo Receiver, and in some ways every device connected. The primary purpose of this thread is to spread some advice I received after tinkering with different solutions for about a month.This surprisingly works, but is apparently not common knowledge. I've seen threads about Kodi/XBMC switching audio devices from WASAPI to DirectSound, and the recommendations have been to buy HDMI splitters or some other device to 'fool' the HDMI handshake. Sure, that solution does work, and may even be a good route to go for some situations, but for I have an easier/cheaper option.
So, the underlying cause of all of these HDMI issues is the Handshake between the receiver and the HTPC. Now, I have an evga Nvidia GTX 970, so I'm certainly not using old hardware. That being said, even top end video cards these days are pitiful when it comes to HDMI audio. So, if you want to know who to blame for these frustrations, there you go. I'm sure M$ is somewhat to blame here as well, but I'm not sure. For example, the $35 Raspberry pi supports a feature called HDMI-CEC, yet these $500 video cards dont. It's ridiculous.
So, when you turn your TV off, Windows goes a bit wonky, and assumes that your audio device has been fully disconnected, not just turned off. This is why things get strange when turning your TV/receiver back on in terms of your audio. So the goal of this fix is to forcibly fool the system into thinking it's still connected.
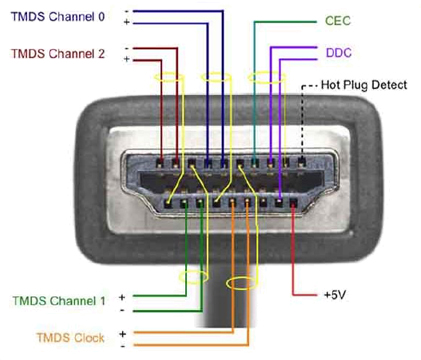
This is the "Pin 19 fix", and it is called that because what you will need to do is cover up pin 19 on your HDMI cable. I can not see why it would matter which end of the cable (where it plugs into the receiver, or where it plugs into the HTPC) is covered, but I personally cover pin 19 on the end that plugs into my HTPC. A tiny sliver of electrical tape, like the image (from a Microsoft blog) shown below, should suffice.
Once you cover up pin 19 you'll want to go ahead and restart your computer. After that, you'll be good to go!
All this does is block the Hot Plug detection, as seem in the image below.
Well, I hope that this information proves to be helpful to others out there who have run into these annoyances.
Monday, March 30, 2020
Friday, January 12, 2018
Remove Google FRP (Factory reset protection) - Tested on OnePlus 3 running Android O
I bought a used OnePlus 3 for a friend and the previous owner had not logged out before wiping the phone so I was faced with the "This device was reset. To continue, sign in with a Google Account that was previously synced on this device" message.
The solution was to boot the phone, tap the Emergency call button and enter/dial *#812# as illustrated in the following video:
The solution was to boot the phone, tap the Emergency call button and enter/dial *#812# as illustrated in the following video:
While searching for a solution I also found the following video with a more "complicated" solution that might be of use if the above does not work:
Friday, August 4, 2017
Launch VM machine on startup Windows Server
I wanted to launch a VM on startup. The way that VMware suggests you do this is by creating a shared VM which was not an option for me as those have some limitations. I tried running VMware Workstation as a service but that didn't quite work either as it would run the VM but when I logged on as the Administrator in Windows Server and try to logon to the VM it would be locked with a message popping up asking if I want to take over.
The solution to this problem was found on a StackExchange Server Fault thread. I am pasting the solution posted by the user Marcus here:
Figured out how to do it myself. It's somewhat of a workaround but that's what I expected to get.
- Alright, first step is to grab a program called AutoLogon.exe from Microsoft:
http://technet.microsoft.com/sv-se/sysinternals/bb963905.aspx
Stop! Don't cringe just yet. Read on...
- Run it, set it so that Administrator should log on automatically.
- Create a task in Task Scheduler. Set it to run only when user (Administrator) is logged on. Trigger is "at log on" and specify that it's only when Administrator logs on.
- Create a second task. Run only when user is logged on, trigger at admin log on. Action should be "start a program" and program is "C:\Windows\System32\rundll32.exe" with the argument field set to "user32.dll, LockWorkStation".
What happens now if you restart the computer is that Administrator automatically logs on, the program you want to start is started and the work station becomes locked. If I log in via Remote Desktop Connection I can see the program window and use the GUI. I can lock/unlock the computer with no problem and disconnect/reconnect as I please. There's no issue if I go to the server and log in at the actual workstation either. Since Administrator is already signed in the task will not run again (it doesn't create some infinite log-in-lock-loop that you can't break out of).
Simple as that. Granted there is a one second time period before the computer becomes locked after the auto login and I guess a pro hacker with physical access to the computer could do something sneaky during this time window but in my case I can overlook that security risk. As long as I don't let any pro hackers into my home and show them the computer the system should be relatively safe. Above all there isn't that much of value on the computer that needs super-vault protection so I'm quite happy with this solution.
Tuesday, August 1, 2017
This virtual machine appears to be in use. - Take Ownership fix
If after a power failure, or reboot of you machine, you encounter the "This virtual machine appears to be in use." message when attempting to connect to your VM's, follow the steps below to remove the message:
- Shutdown VMware.
- Locate the folder where your VM is stored.
- Locate one or more .lck or .lock files and delete them. If you are uncomfortable deleting these files, back them up in a separate folder.
- Restart VMware and run your VM.
The message should not appear.
Delete all files of a specific extension from the directory that is executed, and all it's subfolders - Ubuntu - OSX
The following commands will affect all files of the specified extension from the directory that is executed, and all it's subfolders. It should work on all UNIX based operating systems:
Execute this command first in order to display all the files that are to be deleted (replace EXT with the desired extension):
Execute this command first in order to display all the files that are to be deleted (replace EXT with the desired extension):
find . -name "*.EXT" -type fExecuting this command will delete the list of files that the previous command returned (replace EXT with the desired extension):
find . -name "*.EXT" -type f -delete
Monday, March 27, 2017
What is /Users/Shared/adi in MacOS
I noticed there was an exclusion in my Time Machine for the folder /Users/Shared/adi that I had not placed there. According to galvanist.com "It is used by the Mac App Store and the new iBooks app."
Pasting here from the source to preserve it. Visit galvanist.com for potential updates:
Pasting here from the source to preserve it. Visit galvanist.com for potential updates:
If you’re running Mac OS X ~v10.8 (or later), you’ve probably got a folder at the path
/Users/Shared/adi. Like me, you might be wondering what it is. I did some googling and got nothing. I dug a little further and found (part of) the answer: It is used by the Mac App Store and the new iBooks app.
In case you’re interested, here are the steps I took to arrive at this answer:
- Googled it. Didn’t get any signal.
- I made a shell loop that checks system packages:
$ (IFS=$'\n' > for pkg in `pkgutil --packages`; do > pkgutil --files "$pkg" | grep --label "$pkg" -H "Users/Shared" > done) com.apple.pkg.Essentials:Users/Shared com.apple.pkg.Essentials:Users/Shared/.localizedNo luck there… - I looked in /Applications (sudo was already authenticated):
$ sudo grep -r 'Shared/adi' /Applications 2>/dev/null # ...20 minutes later... $Rats. - Finally, I looked for sandbox entries:
$ grep -rl 'Users/Shared/adi' /System/Library/Sandbox /System/Library/Sandbox/Profiles/com.apple.bookstoreagent.sb /System/Library/Sandbox/Profiles/com.apple.storeagent.sbBingo! com.apple.bookstoreagent is obviously used by iBooks.app. But just to be extra sure:$ grep iBooks /System/Library/Sandbox/Profiles/com.apple.bookstoreagent.sb (regex #"/Library/Preferences/com\.apple\.iBooksX\.secure\.plist$") (regex #"^/private/var/folders/[^/]+/[^/]+/[A-Z]/com\.apple\.iBooksX"))And com.apple.storeagent is used by the Mac App Store:$ egrep -i 'app.?store' /System/Library/Sandbox/Profiles/com.apple.storeagent.sb (regex #"/Library/Preferences/com\.apple\.appstore\.plist$") (regex #"/Library/Caches/com\.apple\.storeagent/updates-com\.apple\.appstore\.updateQueue\.plist$")) (regex #"/Library/Application Support/App Store(/|$)") (regex #"/Library/Logs/appstore\.log$") (regex #"/Library/Preferences/com\.apple\.appstore\.plist$") (regex #"^/private/var/folders/[^/]+/[^/]+/[A-Z]/com\.apple\.appstore") (global-name "com.apple.appstore.CKSignInPrompt.hostclient") (global-name "com.apple.dock.appstore") (right-name "system.install.app-store-software") (right-name "system.install.app-store-software.standard-user")
Update
Thanks to a helpful anonymous commenter for pointing out that it wasn’t just 10.9 and iBooks.
I’ve been wondering about the name adi, and the possibility that it could be “Apple Distribution International”, the apple business unit responsible for electronic download sales. I’ve got no idea. That’s just wild guess that I don’t have much faith in myself.
CommerceKit
We already have a link between ADI and the Mac App Store & iBooks Store.
- “/Users/Shared/adi” appears under
/System/Library/Sandbox/Profilesincom.apple.storeagent.sbandcom.apple.bookstoreagent.sb. storeagentandbookstoreagentappear in the apple privateCommerceKit.framework% locate storeagent [...] /System/Library/PrivateFrameworks/CommerceKit.framework/Versions/A/Resources/bookstoreagent /System/Library/PrivateFrameworks/CommerceKit.framework/Versions/A/Resources/storeagent [...]CommerceKitis used by theApp Store,Apple Configurator, andiBooksapps:% for app in /Applications{,/Utilities}/*.app/Contents/MacOS/*; do (otool -L "$app" | grep -i -H --label "$(basename $app)" 'CommerceKit') 2>/dev/null done App Store: /System/Library/PrivateFrameworks/CommerceKit.framework/Versions/A/CommerceKit (compatibility version 1.0.0, current version 232.0.0) Apple Configurator: /System/Library/PrivateFrameworks/CommerceKit.framework/Versions/A/CommerceKit (compatibility version 1.0.0, current version 135.6.0) iBooks: /System/Library/PrivateFrameworks/CommerceKit.framework/Versions/A/CommerceKit (compatibility version 1.0.0, current version 232.0.0)CommerceKit’s code contains these method references toadi% strings /System/Library/PrivateFrameworks/CommerceKit.framework/Versions/A/CommerceKit | grep adi [some items omitted for bloggish reasons] _adiActionInResponse _adiSilentActionRetryCount %@: Saw ADI action in response to %@, set _adiActionInResponse=YES
CoreADI
You might also note that there’s a
CoreADI framework:/System/Library/PrivateFrameworks/CoreADI.framework
/System/Library/PrivateFrameworks/CoreADI.framework/CoreADI
/System/Library/PrivateFrameworks/CoreADI.framework/Resources
/System/Library/PrivateFrameworks/CoreADI.framework/Versions
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A/CoreADI
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A/Resources
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A/Resources/Info.plist
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A/Resources/version.plist
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A/_CodeSignature
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/A/_CodeSignature/CodeResources
/System/Library/PrivateFrameworks/CoreADI.framework/Versions/Current
And a receipt:
/private/var/db/receipts/com.apple.pkg.CoreADI.bom
/private/var/db/receipts/com.apple.pkg.CoreADI.plist
There is very little information in those files… even extracting text strings from the binary gives very little info. There are some references to encryption.
Its dependencies:
% otool -L /System/Library/PrivateFrameworks/CoreADI.framework/CoreADI
/System/Library/PrivateFrameworks/CoreADI.framework/CoreADI:
/System/Library/PrivateFrameworks/CoreADI.framework/CoreADI (compatibility version 1.1.0, current version 1.34.0)
/usr/lib/libcrypto.0.9.8.dylib (compatibility version 0.9.8, current version 44.0.0)
/System/Library/Frameworks/Foundation.framework/Versions/C/Foundation (compatibility version 300.0.0, current version 833.25.0)
/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation (compatibility version 150.0.0, current version 635.21.0)
/System/Library/Frameworks/IOKit.framework/Versions/A/IOKit (compatibility version 1.0.0, current version 275.0.0)
/System/Library/Frameworks/CoreServices.framework/Versions/A/CoreServices (compatibility version 1.0.0, current version 53.0.0)
/usr/lib/libSystem.B.dylib (compatibility version 1.0.0, current version 159.1.0)Sunday, May 25, 2014
Disable Narrator keyboard shortcut in Windows 8
I have pressed Win Key + Enter many times while attempting to press Alt + Enter, and every time I have to listen to the Narrator speak out the process of me closing the narrator. Here is how to disable the narrator keyboard shortcut by disabling access to Narrator.exe.
Now you should be able to change the permissions of the file, this is where we remove all the permissions from your user and the user back to system, this way your user will not be able to start the Narrator.
- Navigate to %systemroot%\System32
- In this folder a file called Narrator.exe is to be found
- Right click the file and choose Properties
- Choose the Security tab and press Advanced
- In the top of the window press Change to change the Owner permissions
- In the text field write your username and press OK to all the dialogs
Now you should be able to change the permissions of the file, this is where we remove all the permissions from your user and the user back to system, this way your user will not be able to start the Narrator.
- Right click the Narrator file again and choose Properties and Security tab
- Press Advanced
- Now that you are the owner you can change permissions for other users. Choose your own user and press Edit
- Remove the Read & Execute and Read permissions and press OK
- Now press Change in the top under Owner and write system in the text field
- Press OK to all dialogs
Subscribe to:
Posts (Atom)